ROSE Insights

How do successful businesses scale their finance and accounting operations as they grow? In this insightful panel hosted by Rose Financial Solutions , leading executives share real-world experiences and proven strategies for evolving finance infrastructure. Moderator: Timothy J. Fargo, CPA Client CFO, Tax Partner, ROSE CFO Rose Financial Solutions Featured Panelists: Jeffrey F. Brown – President & Founder, XCAL Shooting Sports and Fitness Wilson Geong – Vice President, Finance and Administration, Prison Fellowship International Topics Covered: How the use of data and KPIs evolves with business growth Changing tech stacks, systems, and technical expertise in scaling companies How industry dynamics impact financial system design The evolving role of the CFO in modern organizations Whether you're navigating rapid growth, modernizing your tech stack, or rethinking the CFO’s role, this discussion offers practical takeaways from leaders who’ve done it. Hear how they built finance and accounting systems that scale — and what they’d do differently knowing what they know now.

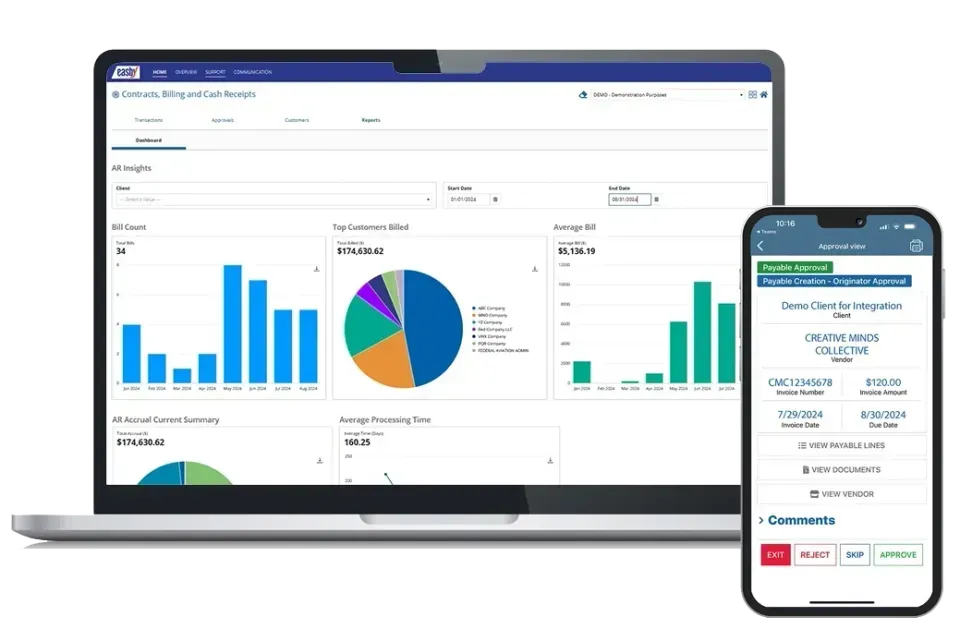
Ted Rose , CEO of Rose Financial Solutions, shares how today’s CFOs can overcome financial bottlenecks and lead with confidence at every growth stage. Learn how Easby and Finance as a Service (FaaS) help automate up to 85% of finance tasks—unlocking real-time insights, compliance, and scalable operations from start-up to $100M+.

Are you a growing business or entrepreneur trying to stay ahead of tax deadlines and avoid costly mistakes? In this video, Ted Rose , CEO and Founder of Rose Financial Solutions, hosts an engaging conversation with Tim Fargo, CPA —a tax expert and Client CFO with over 30 years of experience helping businesses stay compliant and plan ahead. Tim Fargo shares practical, easy-to-follow tax planning tips to help your business: Avoid common tax pitfalls Stay compliant with IRS rules Prepare for audits with confidence Plan ahead for growth and tax efficiency With decades of experience in finance, nonprofits, and the construction industry, Tim breaks down what business owners need to know to make smarter financial decisions and reduce tax season stress. Whether you’re scaling fast or just starting out, this video gives you the expert CFO advice you need to manage your taxes the right way.

Wally Angel (Rose Financial Solutions) and Cedric A. Powell (Sheppard Mullin), moderated by Ted Rose , discuss how mergers and acquisitions expose critical business risks—especially in finance and legal operations. Whether you're planning for an M&A transaction or simply want to strengthen your business operations, this conversation explores key challenges business owners face, including: Corporate hygiene practices companies often overlook Common employment law pitfalls Regulatory regimes frequently misunderstood or ignored Crucial pre-transaction reviews for financial and legal health These missteps can result in lost revenue, missed opportunities, and serious compliance failures—particularly in government contracting, where the stakes are high and regulations are ever-changing. Learn how successful companies are bridging gaps between legal and finance to build stronger, more resilient organizations that can scale confidently and stay compliant.

In this video, Ted Rose discusses the future of finance and accounting automation, highlighting how 85% of Finance and Accounting tasks can be automated by 2030. He addresses common challenges faced by government contractors and growing businesses, such as delayed monthly closings, compliance worries, and financial inefficiencies. Ted introduces Rose Financial Solutions' AI-powered platform, Easby, and their Finance as a Service (FaaS) solution, which promises real-time financial clarity, improved compliance, and scalable financial operations. Learn how Rose Financial Solutions can enhance your team's capabilities, integrate seamlessly with existing systems, and help you achieve financial confidence and growth.
Get More Financial Insights
Ready to gain financial clarity and take control of your financial future? Reach out to us now by filling out this contact form. Our team is here to answer your questions and guide you toward a brighter financial horizon.
Let's start the conversation today!